Last week I needed to analyze traffic form a Virtual Server hosted on a ESX machine. Normally this job would be a piece of cake if the server has his own NIC. But the way with an “old” hub or with an port mirror (port spanning) do not work with a vSwich (a virtual switch on the ESX server).
In this blog post I will describe how to Analyze the traffic of an virtual windows server 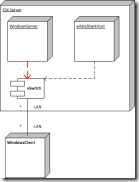 with WireShark (Freeware Packet Analyzer http://www.wireshark.org/ ) on an ESX host . On the UML deployment diagram it is the red dependency witch will be monitored.
with WireShark (Freeware Packet Analyzer http://www.wireshark.org/ ) on an ESX host . On the UML deployment diagram it is the red dependency witch will be monitored.
I use Wire Shark since many years and I find it one of the best Analyzer in the market. Wire shark is also cross platform it runs on Windows, Linux & OSX. I used Ubuntu (http://www.ubuntu.com/) as host for the sniffer because its free and easy to use. The sniffing software should never installed on the productive system!
The Ubuntu VM (Virtual Machine) must be connected to same vSwich as the server you want to monitor.
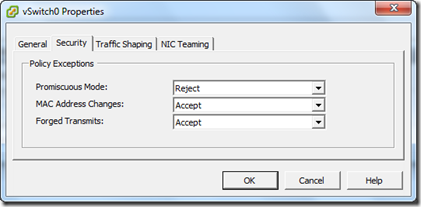
After you have installed the sniffing machine we need to edit the Virtual switch from the ESX server. The good news is that you don’t have any interruption on any VM. Its totally save to do on a Productive system (it only sets the switch form Layer 2 Mode in Layer 1 Mode on the OSI/ TCP/IP Modell) . Open vSphere Client and go to the Network Settings of the vSwitch and click on “Properties…”
Select the vSwitch and click on “edit”.
go to the “Security” tab an change the “Promiscuous Mode:” to “Accept”. The default value is Reject like in the screenshot.
Now the system is reedy to chapter the network traffic. Like you see in the last screenshot the ICMP Traffic (Ping) to an server in the World Wilde Web.